Written by: Amy Boawn, Principal – Head of Fraud Fusion Capability & Lauren Gowdy, Senior Associate – Cyber Fusion and Intel Leader
Fraud: A Growing Problem
Cyber fraud is a growing challenge as fraudsters leverage advanced techniques such as artificial intelligence (AI) to bypass automated verification systems. As a result, more Chief Information Security Officers (CISO) and Advanced Cyber Defense Teams are being asked to solve the identity and authentication challenges associated with cyber fraud.
Today’s fraudsters are sophisticated and often have the upper hand. They operate as organized businesses, complete with data-sharing and research and development efforts. As a result, these “bad actors” have access to vast stores of intelligence, which they exploit through cyber techniques. Social engineering and business email compromise, which continue to gain traction, allow fraudsters to obtain and use legitimate credentials to access accounts, making them nearly impossible to detect by traditional means.
Current Solutions Are Ineffective
Traditional fraud prevention and detection methods are ill-equipped to handle the tactics, techniques, and procedures (TTP) being used by today’s threat actors. Specifically, fraud, cybersecurity, threat intelligence and analytics teams at most organizations do not typically collaborate and their tools and protocols are not synced to enable proactive detection. They speak different languages, have different workflows, and generally stick to their own spaces. When cyber teams notice something suspicious, they don’t always share their intelligence with the fraud team, and vice versa. Because fraud now cuts across the responsibilities of cyber and fraud teams, lack of communication can lead to security teams addressing a single threat actor using two different approaches.
Another issue with traditional fraud solutions is that they are reactive by nature. Action is taken after fraud occurs, leaving less time to track and escalate a fraud incident before losses are incurred. Many times, organizations have already suffered a loss and the only recourse is a post-mortem assessment. By the time new controls are implemented for that particular tactic, adversaries have moved on to a new technique.
Bridging cybersecurity, threat intelligence, analytics and fraud prevention is critical to maintaining the integrity of an organization’s overall security posture, as well as matching the dangers posed by the convergence of cyber and fraud from a threat actor perspective. This is where the fraud fusion center construct can create an environment for cyber and fraud professionals to work together and create effective detection, prevention, and response to fraud activity, and shift the focus from reactive to proactive mitigation. As depicted in Figure 1, proactive efforts allow for fraud to be detected and prevented prior to the transaction. Once money has been moved, the only action to be taken is reactive.
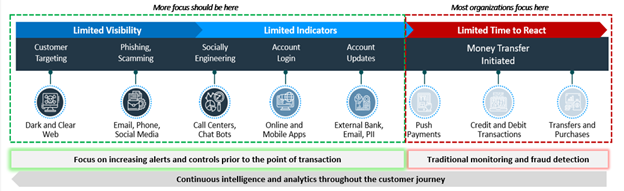
Figure 1 – Fraud killchain (pre-payment indicators in blue, post-payment indicators in red)
The Fraud Fusion Approach
A fraud fusion center is a next-generation security operations center (SOC) that brings cyber threat intelligence and cyber defenders together with fraud specialists to create a continuous loop of information exchange. This “fused” team hunts for threats across domains and shares data, surveillance technologies, and case management tools. It leverages advanced analytics, repeatable processes, and workflow automation/orchestration tools to accelerate manual actions.
The fraud fusion center model, as depicted in Figure 2, not only leverages traditional cyber fusion and fraud operations, but taps into threat intel, advanced analytics, monitoring, and response. The benefit of this is that it facilitates the sharing of monitoring operations. When an anomaly or fraudulent activity is detected, the time to respond can be positively impacted with the fraud fusion concept. This allows for faster and more effective action than waiting for coordinated responses from individual tools and team members.
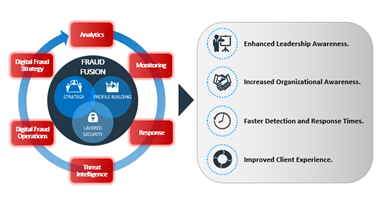
Figure 2 – Fraud fusion center components
Steps For Success
Building a fraud fusion center requires a paradigm shift. It means cyber and fraud teams must speak the same language, understand (and agree upon) different levels of compromise, and be willing to work together to effectively share data, people, and processes. While this transformation can take a year or even longer to achieve, there are some immediate steps organizations can take to enhance their fraud prevention programs: these can be divided into “quick wins” and “strategic actions.”
Quick Wins:
Find a champion.
A champion should be a senior leader or executive who can champion the program and lead change management. This person must have the authority to mandate and create a fraud fusion center. Without this level of sponsorship, organizations spend a lot of time and energy making very little progress.
Take stock of existing capabilities.
Fraudsters know the weaker links in technology: organizations with softer controls are the targets because fraud rings are hitting everyone equally—every bank across the board. Organizations must take inventory of what they have and benchmark their capabilities against their peers and established good practice.
It is vital that organizations understand what technologies they have and who is benefitting from their outputs. Often, the fraud and cyber teams are using similar tools that would be more effective at combating fraud if both teams had access to the outputs, e.g., both teams sharing the same SIEM (security information and event management) tool and log data.
Partner a fraud analyst with the CTI team (or vice versa)
By partnering together, fraud and cyber threat intelligence (CTI) analysts can quickly coordinate efforts and leverage their combined expertise. This results in greater insight into threat actor patterns, indicators of compromise, and potential large-scale fraud campaigns.
Strategic Actions:
Define a strategy and communicate often.
Begin by identifying the commonalities between the fraud and cyber teams. Build a strong foundation of shared indicators of compromise that leverages response workflows, analytics, data sets, and coordinated responses for faster action. Document the strategy and communicate it early and often.
Nail several use cases.
Identify a few fusion center use cases and pilot them successfully. For example, start with monitoring account takeovers (ATO) in a specific channel during a defined timeframe using a specific method. Once it’s possible to demonstrate success and consequently gain traction and support, the efforts can be expanded.
Fuse the data.
Combining disparate data sources too soon can create a lot of false positives and messy data lakes. It’s easier to keep data separate until it is understood what types of fraud are being seen and the processes that work to address them; then, it is possible to start fusing data a little at a time. Leverage feeds already in existence, when possible.
Layer technology solutions and establish a baseline.
Let the analytics platform run to get a baseline, and then determine what success will look like for the fraud fusion center. Determine what type(s) of fraud are being detected, what time is needed to respond, and how many fraudulent attempts are being blocked. These metrics will help demonstrate success.
Evaluate often.
Assess how the fraud and cyber teams are collaborating and where there is room for improvement. After an alert or event, make the appropriate process changes to enable the fraud fusion center to proactively detect that fraud in the future.
Keep it consistent.
Repeatable processes for monitoring, alerting and responding to fraud are necessary. Responding to fraud consistently and feeding information back into data sets will reduce false positives and improve a fusion center’s ability to catch new fraud.
Conclusion
As fraudsters continue to utilize cyber techniques at an increasing and more complex rate, the need to adopt a holistic solution grows more urgent. A fraud fusion center will help the company establish the process and tools to communicate across capabilities, transition reactive approaches to proactive ones, and help stop fraudulent activity from disrupting successful operations.
About Booz Allen
For more than 100 years, military, government, and business leaders have turned to Booz Allen Hamilton to solve their most complex problems. As a consulting firm with experts in analytics, digital, engineering, and cyber, we help organizations transform. We are a key partner on some of the most innovative programs for governments worldwide and trusted by its most sensitive agencies. We work shoulder to shoulder with clients, using a mission- first approach to choose the right strategy and technology to help them realize their vision.
